Security Risk Management
Compliance Management
Security Awarness Training
Business Continuity Planning (BCP)
Business Impact Analysis (BIA)
Information Security Audit
Information Security Management
Information security Governance
Security policies (Acceptable usage policy, Mobile device Policy, Network security Policies... etc .. etc)
Security Incident Response Planning
Disaster recovery policies
Compliance monitoring: GDPR, SOX, HIPAA, PCI-DSS, FedRAMP, CCPA
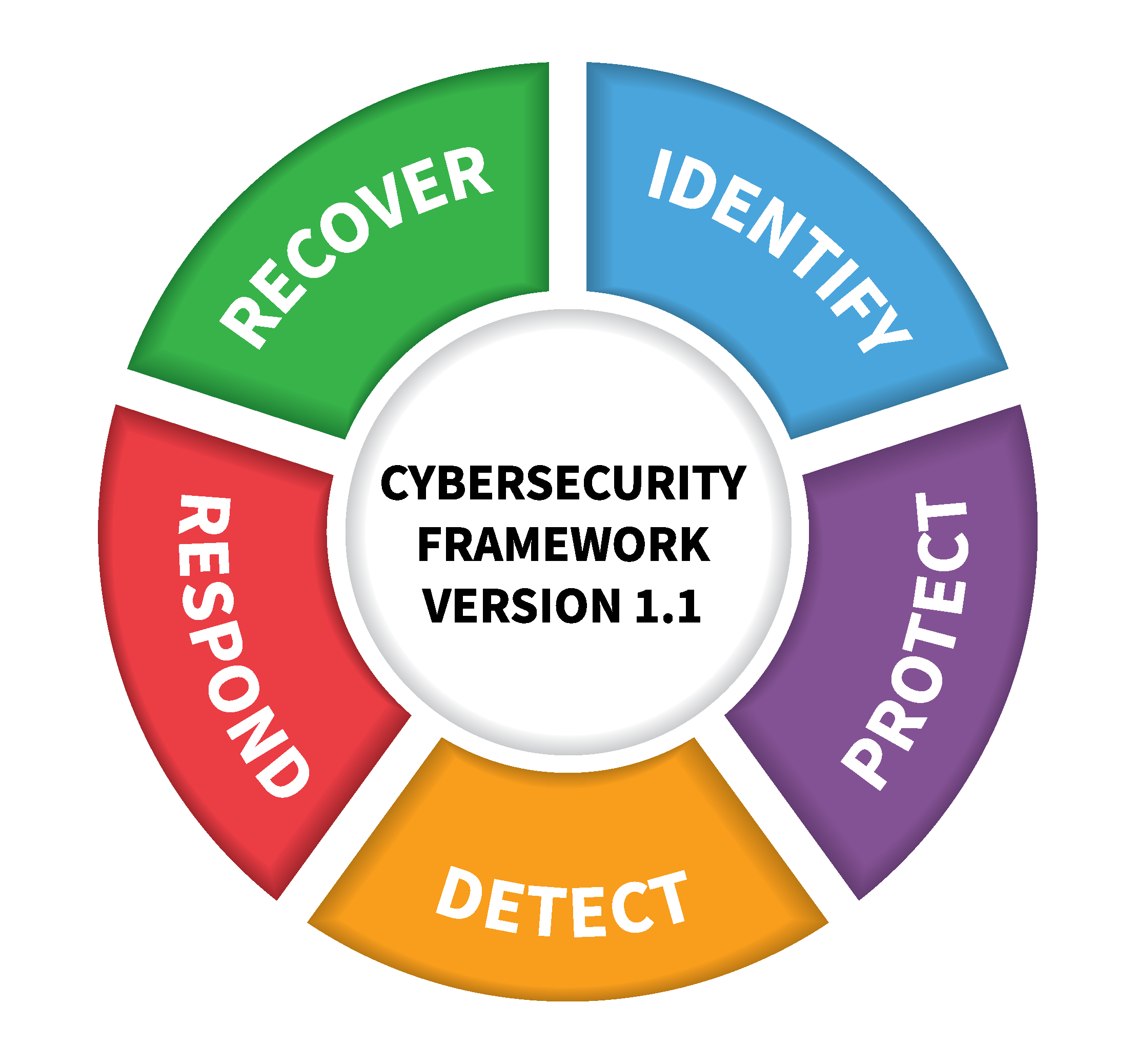
Security frameworks: NIST CSF, ISO/IEC 27001, SOC2
Asset management
Asset risk profile
Global risk register
CISO And VCISO Advisory
Threats modeling/landscaping
We offer pre-compliance reviews for your IT infrastructure. Providing guidance
and mitigation strategies for any relevant non conformance